Enviado por
common.user1374
Technology

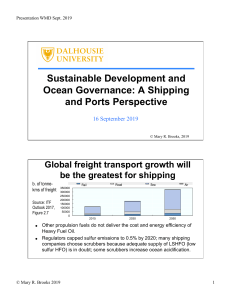
Technology, Information and Resilience Risk Primer for 2019 Published: 5 February 2019 ID: G00375911 Analyst(s): Earl Perkins, Roberta Witty, Jie Zhang Risk management identifies an organization’s hazards to achieving success. Security and risk management leaders must rethink how continuous change requires new approaches to the risk-security relationship. Scope Information and technology now serve as tool and product, changing in value, volume, variety and velocity. Organizations must change in approach and skill to meet the new risks and security demands. Some topics within this initiative include: ■ Resilience ■ Risk management ■ Privacy ■ Business continuity ■ Cyber-physical security Analysis Figure 1. Technology, Information and Resilience Risk Overview Source: Gartner (February 2019) Organizations are moving from just responding to technology changes to creating a resilient 1 ecosystem that embraces change. Gartner’s “ContinuousNext” formula envisions an informationrich organization driven by five key imperatives: augmented intelligence, culture, digital product management, digital twins and privacy. The ContinuousNext formula is a response to continuous change in risk management. The very nature of the risk and business relationship changes as well. Risk management becomes 2 more digital and integrated, and business imperatives become more cyber-physical. For both risk and business practices to be efficient and effective, organizations need an approach that leverages the risk-business relationship. Organizational resilience — the ability of an organization to resist, absorb, recover from and adapt to business disruption — is the cornerstone of any risk-security relationship. To deliver that resilience, a coordinated system of information, technology and operations provides the business with security, preserves data privacy and ensures continuity of operations. Organizations must continuously analyze their risk exposure and environment. They may leverage risk-data Page 2 of 10 Gartner, Inc. | G00375911 management for decisions about setting security priorities and reporting on risk to audit stakeholders. Factors such as leadership, culture, governance and skills development aid in ensuring the success of the risk-security relationship. In 2019, the theme continues to be one of continuous and accelerated change — in technology and in business relationships and practices. Restructuring the risk-business relationship with new and updated practices is mandatory to reflect and maintain how organizations respond to that change. Determining and obtaining the necessary resources to do so ensures a higher probability of success for managing risk, securing cyber and physical ecosystems, and, most important, protecting the business. Top Challenges and How Gartner Can Help Risk management processes aren’t positioned for a rapidly changing regulatory environment, which impacts achievement of the organization’s strategy and objectives. Restructuring the risk management program to more nimbly adapt to these changes should be the goal. Many risk decision makers haven’t been educated on effective risk management decision making. Many risk decisions have also been automated, and the risk processes supporting those decisions haven’t been restructured to account for this. Security policies are too broad and don’t drive effective risk decision making, and the cyber-physical security practice has not yet become a more effective consultant for those decision makers. Risk isn’t communicated effectively to senior business leadership as a result. Organizations must remake the risk-business relationship in the image of the business for leadership to succeed. The topics we cover include these areas: ■ Resilience: Develop organizationally resilient business planning and operations to address risk and security needs. ■ Risk management: Design and deploy a risk management program with fit-for-purpose frameworks, technology choices and organization. ■ Privacy: Address privacy concerns through program management and effective technology use. ■ Business continuity: Deliver business continuity and disaster recovery capabilities for business and IT. ■ Cyber-physical security: Leverage digital transformation with a cyber-physical security practice around technology, process and organization. Some content may not be available as part of your current Gartner subscription. Contact an Account Executive if you wish to discuss expanding your access to Gartner content. Our research addresses the following common client questions: Gartner, Inc. | G00375911 Page 3 of 10 How can we develop and manage organizational resilience as part of risk management? Gartner research has found that current risk management plans fail to account for the organization’s ability to absorb, recover and adapt to digital transformation. For example, many risk plans draw only cursory links between business continuity and risk, raising the possibility that plans could fail to account for known risks. Likewise, risk plans have incomplete means to quickly and accurately assess digital risk costs. Emerging trends in performance-to-risk indicator mapping underscore a new approach to resilient risk practice. Certification activities can inform best practices for maturing risk management to a resilient state. During events that can disrupt an organization’s business, better communication to risk accountability owners and influencers can lead to improved resilience. Planned Research ■ Organizational Resilience Strategic Roadmap ■ Communicating to Different Constituents During a Crisis ■ Making the Business Case for Organizational Resilience by Applying Risk-Adjusted Leading Performance Indicators How can we design and deliver business-relevant risk management frameworks, metrics and systems? The design and delivery of effective risk management practice is a critical objective for security and risk management (SRM) leaders. They need a formal approach to define business-relevant risk, measure it and operate systems around it for the organization’s business users and providers of technology. A wide range of process steps, tools and controls must be available, including updated risk heat maps, guides for the business-technology approach to risk, processes for complex and varied service environments, and systems for risk quantification. Planned Research ■ Toolkit: A Practical Risk Heat Map That Drives Change and Growth ■ From GRC to Integrated Risk Management: A Practical Guide ■ Managing Vendor Risk to Ensure Digital Business Success ■ Opportunities and Challenges in Cyber Risk Quantification ■ Magic Quadrant for Integrated Risk Management What can we do to provide an effective compliance and audit process and tools to stay relevant to an evolving digital business environment? The continuously evolving business requirements and subsequent transition in technology decisions impact applicable compliance mandates and challenge the effectiveness of existing risk remediation strategies. SRM leaders continue to need capabilities for optimizing and realigning due diligence activities in their digital ecosystem. Gartner research continues the practice of updating advice Page 4 of 10 Gartner, Inc. | G00375911 regarding frameworks that inform compliance and audit activities. Evolving roles in governance and management are also addressed. Notable reset approaches in auditing affected by environments such as the cloud, application development and operations will be examined. Addressing technology and service changes in support of assurance activities and audit systems will also be core topics for leaders in business and technology support. Planned Research ■ Toolkit: Job Description for the Digital Compliance Officer ■ How to Audit Agile Approaches in DevOps ■ FedRAMP Demystified ■ Best Practices in Implementing the NIST Cybersecurity Framework What are the components of best-in-class privacy programs, and how do we enable privacy compliance for our organization? Gartner research examines the governance and control necessary to ensure privacy and trust in business interactions for organizations and people. Privacy management programs have people, business, technology and legal drivers. Digital transformation also forces privacy programs to address the continuous changes needed to stay ahead and remain practical. Innovations in data privacy will address key technological changes in areas such as analytics, artificial intelligence and integrated risk management. A growing and complex regulatory environment also continues to place demands on privacy management that must be addressed. An encompassing privacy architecture is required to participate fully in the ContinuousNext formula for 2019 and beyond. Planned Research ■ Practical Privacy — Data Mapping, Going From Manual to Continuous Discovery ■ Six Security Technologies That Are Key to Operationalizing Privacy ■ Five Areas Where AI Can Supercharge Your Privacy Readiness ■ Evolving Toward a Comprehensive Privacy Architecture for Data and Analytics How do we ensure business continuity, disaster recovery and crisis management, and what technologies and services are required to do so? Business continuity management programs are broad, addressing recovery, crisis/emergency management, disaster recovery, and supplier risk and contingencies. Few programs in an organization affect as many stakeholders: customers, partners, suppliers and employees. Few programs are so pervasive across facilities and supporting systems such as IT/OT and data, including vital records. Business continuity management (BCM) is also central to ensuring organizational resilience in the enterprise and supplier ecosystem. Gartner research seeks to deliver a strategic roadmap for clients and to identify how elements of BCM processes are used. Advice Gartner, Inc. | G00375911 Page 5 of 10 regarding use of new technologies to address engagement practices, regulatory requirements and collaboration functions is also provided. Gartner continues to expand research into markets for crisis/emergency management platforms and notification services. Planned Research ■ BCM Strategic Roadmap ■ How Artificial Intelligence and Machine Learning Are Changing the BCM Profession ■ Best Practices for Developing Business Workaround Procedures Following a Cyberattack Outage ■ ISO 22301:2012 Organizational Certification and Best Practices — Certification vs. Resilience How can we deliver a cyber-physical security practice around technology, process and organization? Gartner is expanding research into the cyber-physical systems (CPS) security initiatives that assetcentric organizations pursue. CPS presents an opportunity to tackle security and safety across IT, OT and Internet of Things (IoT) through transformation initiatives specific to vertical industry needs. Strategy, governance and tactics for business models and direction aid relevant SRM leaders to address specific needs of CPS. Those needs include identifying vertical requirements for strategic security and safety concerns, operational changes, and risk management. Planned Research ■ Key Considerations for Developing a Security Vision and Strategy for Cyber-Physical Systems ■ How Cyber-Physical Systems Stretch Traditional Vulnerability and Threat Considerations ■ Using the Gartner Vertical Strategy Framework to Position Cyber-Physical Systems Security as a Business Imperative Page 6 of 10 Gartner, Inc. | G00375911 Related Priorities Table 1. Related Priorities Priority Focus Vendor Management Strategy and Operations Vendor management strategy and operations help mature the organization’s ability to assess, monitor and manage vendor performance, risks, relationships and contracts in pursuit of business goals. Identity and Access Management IAM encompasses tools and best practices to manage identities and access across an enterprise's workforce and customers, to manage risk, reduce fraud and other losses, and enable business imperatives. Security of Applications and Data This initiative enables organizations to conduct business and venture into new opportunities by managing security risks against their most exposed and valuable assets, namely applications and data. Information Security Management Program Gartner delivers timely and comprehensive guidance for information security management programs for organizations. That guidance is prescriptive and targets key initiatives for best-in-class programs. Source: Gartner Suggested First Steps ■ “Leadership Vision for 2019: Security and Risk Leader”: This slide deck will help SRM leaders in planning for 2019 and in presentations to leadership, peers and teams. ■ “Build for Privacy”: Successful SRM leaders need to support their business objectives with “privacy engineering” to gain a competitive advantage and differentiate offerings in crowded markets. ■ “The Resilience Premium of Digital Business: A Gartner Trend Insight Report”: SRM leaders must deliver by building a culture of systemic resilience through viewing resilience as a premium and not as a cost. ■ “Top Security and Risk Management Trends”: SRM leaders must take advantage of emerging trends to improve resilience and elevate their standing in the organization. ■ “Definition: Business Continuity Management”: SRM leaders responsible for business continuity need to understand the full scope of their BCM efforts, which should comprise an enterprisewide program. ■ “The Business Impact Analysis: A Digital Business Essential”: SRM leaders should use a crossfunctional BIA as an essential tool in developing collaborative procedures in response to a major business disruption. ■ “Organizational Resilience Is More Than Just the Latest Trend”: SRM leaders must work with the whole organization to design, implement and maintain resilience characteristics to ensure digital business initiatives become sustainable operations. Gartner, Inc. | G00375911 Page 7 of 10 ■ “Ensure Digital Business Resilience Through Better Risk Management Planning”: To achieve organizational resilience, SRM leaders must consider impacts on roles, responsibilities and external relationships resulting from new participants, technologies and processes. ■ “The Organizational Resilience Program Delivery Model”: SRM leaders must work with the whole organization to design, implement and maintain resilience characteristics to transform digital business initiatives into sustainable operations. ■ “Delivering Resilience and Recoverability for Distributed Transactions Poses a Whole New Challenge”: As digital business software embraces heterogeneous distributed transactions and microservices, application leaders need new means of ensuring data and process integrity. ■ “Cybersecurity Redefined for the Digital Era”: SRM leaders must agree on what cybersecurity means to address the risks and threats of digital transformation. ■ “Focus More on the Realities of Cyber-Physical Systems Security Than on the Concepts of IoT”: To be effective, SRM leaders must holistically address the needs of cyber-physical systems rather than focusing on specific implementations of IT, OT or IoT security. Essential Reading ■ “Critical Capabilities for Integrated Risk Management": SRM leaders can use this research to evaluate IRM solutions to address a business-unit-wide view of risk and compliance. ■ “Magic Quadrant for Integrated Risk Management”: SRM leaders should use this Magic Quadrant to identify solutions that support an integrated approach to risk management. ■ “Maverick* Research: Why GDPR and Other Privacy Initiatives Will Fail”: CIOs and IT leaders should be aware that difficulties and challenges may lead these regulations to fail. ■ “From Digital Transformation to ContinuousNext: Key Insights From the 2018 Gartner Symposium/ITxpo Keynote”: CIOs can prepare their organizations for continuous change by focusing on five imperatives: augmented intelligence, privacy, culture, digital product management and digital twins. ■ “Critical Capabilities for IT Risk Management Solutions”: SRM leaders experience increased demand for ITRM solutions originating from cybersecurity initiatives. ■ “Predicts 2019: The Ambiguous Future of Privacy”: These predictions highlight for SRM leaders the correlation between new technology and regulatory impact, customer dependency and commercial opportunity. ■ “Cool Vendors in Security and Risk Management: Securely Scaling Digital Businesses”: SRM leaders striving to balance assurance against scaling business operations should evaluate these solutions. ■ “Manage the Digital Risks of Blockchain Initiatives”: SRM leaders require digital risk thinking and action to address blockchain risk. ■ “Leverage Emotions to Communicate Risk More Effectively”: Understanding risk sentiment helps SRM leaders craft more meaningful risk messaging. Page 8 of 10 Gartner, Inc. | G00375911 ■ “Learn Your Risk Appetite or Fail at Risk Management”: SRM leaders need to work with business stakeholders to determine organizational risk appetites. Tools and Toolkits ■ “Toolkit: Conducting a Business Impact Analysis”: SRM leaders should use this Toolkit to capture and analyze the data needed to determine the recovery priorities that will drive recovery strategies and solution development. ■ “Toolkit: Assessing the Effectiveness of Recovery Plans Following a Business Disruption”: This user-customizable Toolkit offers SRM leaders and their enterprises an easy way to assess the effectiveness of their plans following a business disruption. Evidence 1 “From Digital Transformation to ContinuousNext: Key Insights From the 2018 Gartner Symposium/ ITxpo Keynote” 2 “Focus More on the Realities of Cyber-Physical Systems Security Than on the Concepts of IoT” Gartner, Inc. | G00375911 Page 9 of 10 GARTNER HEADQUARTERS Corporate Headquarters 56 Top Gallant Road Stamford, CT 06902-7700 USA +1 203 964 0096 Regional Headquarters AUSTRALIA BRAZIL JAPAN UNITED KINGDOM For a complete list of worldwide locations, visit http://www.gartner.com/technology/about.jsp © 2019 Gartner, Inc. and/or its affiliates. All rights reserved. Gartner is a registered trademark of Gartner, Inc. and its affiliates. This publication may not be reproduced or distributed in any form without Gartner's prior written permission. It consists of the opinions of Gartner's research organization, which should not be construed as statements of fact. While the information contained in this publication has been obtained from sources believed to be reliable, Gartner disclaims all warranties as to the accuracy, completeness or adequacy of such information. Although Gartner research may address legal and financial issues, Gartner does not provide legal or investment advice and its research should not be construed or used as such. Your access and use of this publication are governed by Gartner Usage Policy. Gartner prides itself on its reputation for independence and objectivity. Its research is produced independently by its research organization without input or influence from any third party. For further information, see "Guiding Principles on Independence and Objectivity." Page 10 of 10 Gartner, Inc. | G00375911